Technical Review of the Anti-Detect Browser Octo Browser
Octo Browser is a modern anti-detect browser designed for secure multi-accounting and online anonymity. It allows the creation of numerous isolated browser profiles, each with its own unique parameters and IP address, preventing websites from detecting that these profiles belong to the same user. In this article, we will thoroughly examine the technical features of Octo Browser: how the profile system and data storage are structured, how browser fingerprints are spoofed, and how proxy server integration is implemented (including an example of using residential proxy networks from 2Captcha).
Octo Browser has a special promotion for users of the 2captcha service - use the promo code CAPTCHA30 it gives a 30% discount on the purchase of the first month of any subscription.
Browser Profiles in Octo Browser: Isolation and Data Security
Octo Browser allows running thousands of independent profiles on a single device. Each profile simulates a separate device and environment, enabling users to work with multiple accounts simultaneously without the risk of bans and without interconnection between them. Key features of profile creation in Octo include:
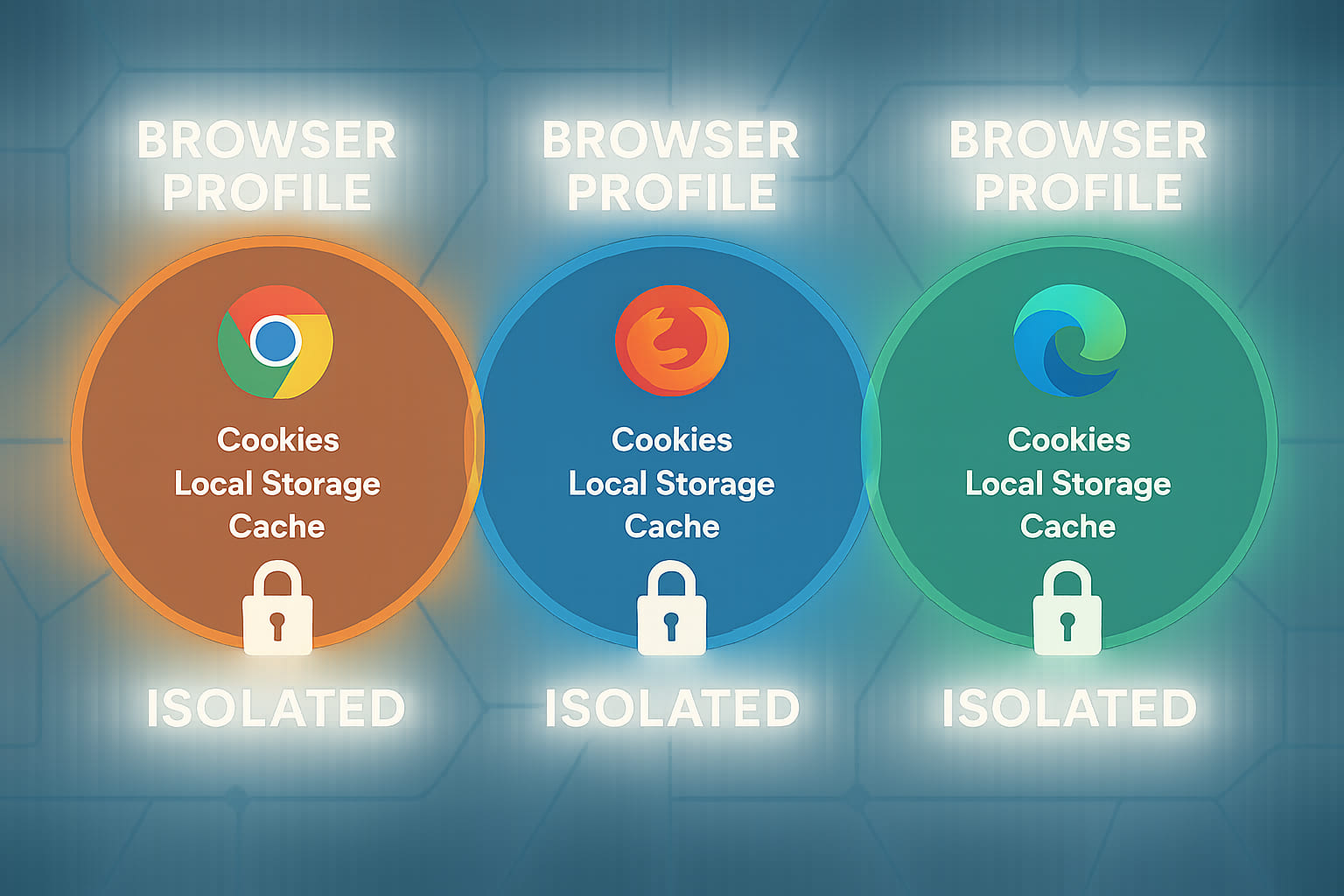
- Complete Profile Isolation: Each profile has its own separate browser context, including cookies, local storage, cache, history, etc. This protects your accounts from mutual influence. A well-configured profile hides any connections between accounts and helps prevent blocking. In practice, each Octo profile has a unique fingerprint resembling a real device, so websites treat it as an independent user
- Quick Profile Creation and Setup: Octo Browser enables the creation of profiles with a single click. The "Quick Profile" function automatically generates a new profile with a pre-configured fingerprint setup. If necessary, each profile can be manually adjusted: you can assign a name, attach a proxy, set up extensions, upload the required cookies, etc. Advanced management features are also available, such as profile templates – you can create a template with specific parameters (tags, proxies, extension sets, icons, and other settings) and then quickly launch multiple profiles based on it.
- Mass Cloning and Import: The import/export tools allow batch processing of profiles. Profiles can be exported in the proprietary .octo format and shared with other Octo Browser users or transferred between devices. Mass profile creation is also supported—up to 100 profiles can be generated at once by specifying parameters via CSV/Excel or templates. This is convenient for large-scale tasks when you need to quickly deploy dozens of new "identities" in the browser.
- Data Storage and Encryption: All profile data is stored in Octo's cloud storage and is securely protected. On the server, information is encrypted using the AES standard and stored in European data centers. An important feature of Octo Browser is the ability to set a password for each profile, enabling end-to-end encryption of profile data. Even Octo employees do not have access to your profiles: they only have access to the contact email of the account, while profile content (cookies, passwords, etc.) is not stored in an unprotected form. These measures minimize the risk of leaks—Octo has had no cases of user data compromise throughout its history.
- Tools for Secure Operation: Octo provides additional features to increase the credibility of profile behavior. For example, the "Paste as Human Typing" function simulates manual typing when pasting text in the browser, so anti-fraud systems don't suspect clipboard insertion. You can also install browser extensions (e.g., MetaMask, CAPTCHA solver extension, Grammarly, analytics add-ons, etc.) inside the profile, just like in regular Chrome. A history of actions (change log) is kept for each profile—up to 100 recent actions are saved and available for review, helping track who made changes and when. For team accounts, collaboration features are available: profiles can be shared with colleagues without risking "breaking" the fingerprint, access rights can be distributed (e.g., profile export restriction, read-only access), and team members' actions can be monitored through an audit log.
It is important to note that the correct setup of a profile is key to its "longevity." Octo Browser recommends setting realistic combinations of device parameters when creating a profile and using proxies that match the profile's geolocation (more on this later). A properly configured profile significantly reduces the chance of a ban and enhances internet anonymity.
Spoofing Browser Fingerprints: Managing Fingerprints in Octo
The main technical component of the anti-detect browser is its fingerprint spoofing system. A fingerprint is a collection of parameters of your device and browser (User-Agent, screen resolution, timezone, font list, WebGL, Canvas, plugin list, hardware characteristics, and more) that websites use to uniquely identify you. Octo Browser provides flexible and reliable management of these parameters, allowing each profile to have a unique "fingerprint." The technical features of fingerprint implementation in Octo Browser are as follows:
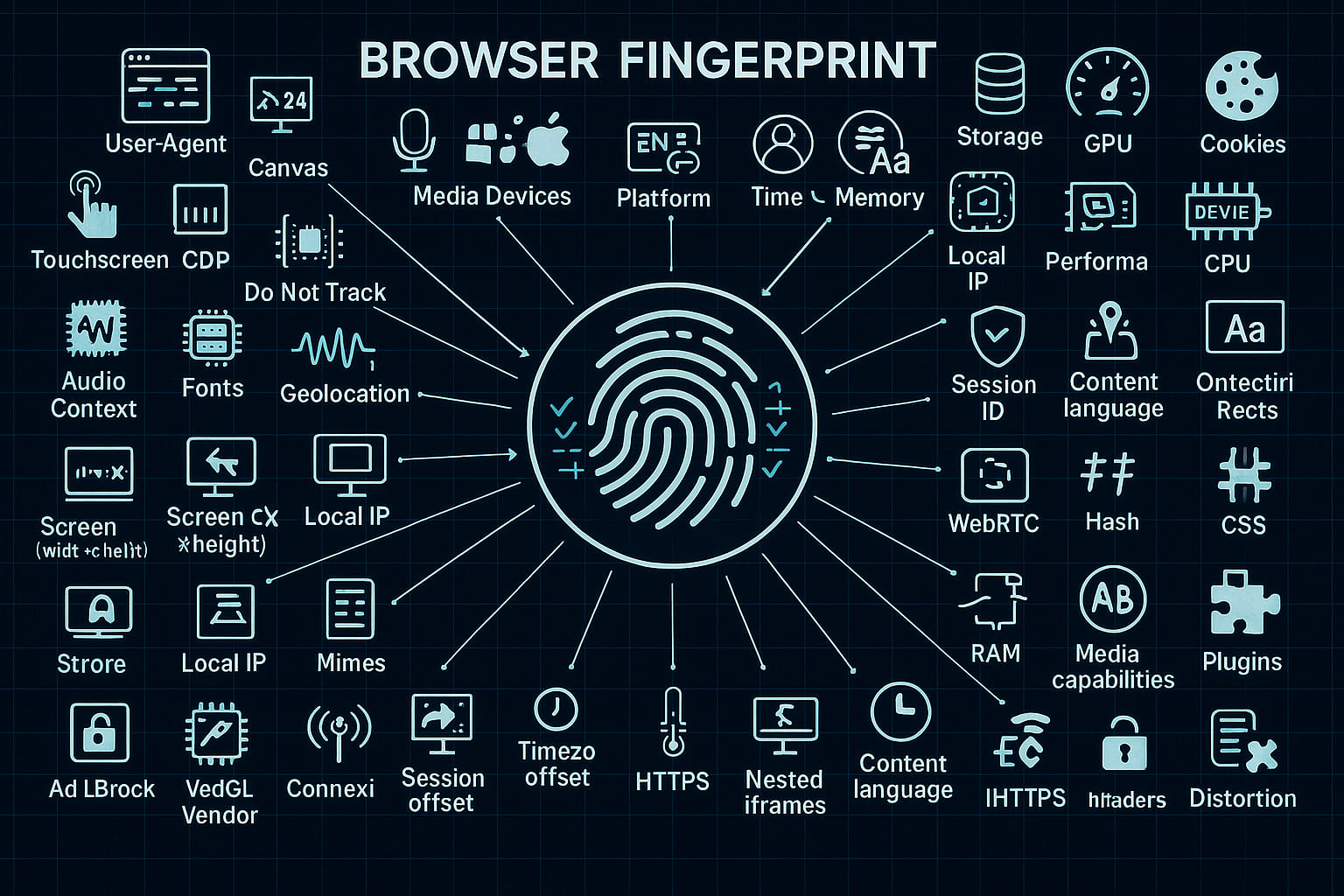
- More than 50 Device Parameters: Octo users can configure over 50 different characteristics of a digital fingerprint for each profile. For advanced cases, fine manual tuning is available – almost everything can be modified, from basic parameters to specific ones. For example, data such as User-Agent (the string identifying the browser and OS), operating system version (Windows or macOS), screen resolution, language settings, timezone, geolocation, CPU cores, RAM size, video card model, WebGL presence, font list, audio/video device information (e.g., simulating the presence or absence of a webcam and microphone), and much more can be adjusted. Even low-level "hardware noise" can be controlled by experienced users to complicate tracking through Canvas/WebGL fingerprints. For standard use, reasonable default values are provided: most parameters are already generated for real devices to make the fingerprint appear credible.
- Generating Realistic Fingerprints: Octo includes a fingerprint generation mechanism that selects compatible parameters. It is important not just to randomly change individual settings, but to form a consistent image of a real device. Octo Browser combines values that are commonly found in existing system configurations, ensuring that the fingerprint doesn't appear suspicious. For example, if the User-Agent is set to Chrome for Windows, other parameters (screen resolution, font list, timezone, CPU type, etc.) will match a typical Windows machine. This approach ensures maximum fingerprint credibility and reduces the likelihood of anti-fraud systems detecting anomalies in the configuration.
- Integration at the Browser Core Level: Octo Browser is based on the Chromium engine, and developers have implemented fingerprint parameter spoofing directly within the browser core. This means that parameters are modified at a low level, not superficially through scripts, making any attempts at detecting modifications ineffective. Anti-fraud scripts on websites cannot "see" that the parameters have been spoofed, because Octo does not just mask them but replaces them at the very source of the data sent to the website. This approach protects against additional checks for spoofing, and the profile's fingerprint appears completely "authentic" to websites.
- Fingerprint Quality Confirmed by Tests: We are confident in claiming that Octo Browser is the only anti-detect browser capable of passing popular fingerprint checkers (such as Pixelscan, BrowserLeaks, Whoer, IP-API) without errors or warnings. These services typically identify inconsistencies and flags ("alerts") if something in the fingerprint looks unnatural. Octo successfully avoids such flags, which indicates a high level of device parameter emulation quality. Users can independently verify their profile on these platforms to ensure there are no "suspicious" parameters. Additionally, Octo has its own R&D department, which constantly analyzes changes in anti-fraud systems on popular websites and promptly updates the spoofing algorithms. For example, when new browser versions are released or new tracking techniques emerge, Octo quickly updates its core (called Octium) and parameters to ensure that Octo sessions do not differ from the latest Chrome sessions. This keeps the anti-detect browser always one step ahead of automated monitoring systems.
- Flexibility and Ease of Setup: While most users are satisfied with automatic fingerprint generation, Octo provides freedom for manual configuration. In the profile interface, you can modify any parameter – from timezone to WebGL driver. There is an option for full randomization (if you need a completely new fingerprint) or the selection of presets. For example, you can synchronize the timezone, language, and geolocation of the profile with the chosen proxy – this is a good practice that reduces suspicion (when the IP and browser geolocation point to the same region). Overall, Octo combines ease of use (for beginners, simply click "Create Profile" to get a ready-to-use fingerprint) with fine control (for experts, dozens of manually configurable parameters are available). This approach satisfies the needs of different user categories and tasks.
Proxy Integration: Unique IP for Each Profile
Simply changing browser parameters is not enough for complete anonymity—you also need to manage the IP address. If all profiles use the same IP, websites will easily link them together. Therefore, Octo Browser pays special attention to proxy server integration. Each profile can be assigned its own proxy, ensuring a unique external IP address and region-specific routing. Here's how this is implemented:
- Support for Various Proxy Types: Octo Browser works with all popular proxy types: HTTP, HTTPS, SOCKS5, SSH, and IPv6 proxies. This offers flexibility in choice—you can use standard data center HTTP proxies or residential or mobile proxies in SOCKS5 format, depending on the task. SSH tunneling is also supported as a special proxy connection type. This wide range of protocols allows integrating almost any proxy service into Octo.
- Convenient Proxy Manager: Octo includes an intuitive proxy management interface for profiles. There is a dedicated "Proxies" section (proxy manager) where you can upload a list of proxies in bulk, save them, test their functionality, and quickly apply them to various profiles when needed. Added proxies are stored in a list with important information (proxy name, associated profiles, protocol, IP address, port, country, provider, timezone, and connection status). You can edit entries, group proxies by categories, and perform bulk actions—for example, check or remove a group of proxies, change IPs for several proxies (if the provider supports it). The built-in checker allows testing proxies with a single click and viewing the result (successful or not) with information about the outgoing IP, provider, location, etc. Statuses are color-coded: green (proxy is active), yellow (not checked recently), red (connection failed).
- Permanent vs. Temporary Proxies: Octo allows assigning two types of proxies to a profile—saved (from the proxy manager list) or temporary. Saved proxies are those you add to your list and can use multiple times across different profiles. Temporary proxies can be specified manually in the settings of a particular profile without saving them to the global list. Temporary proxies are convenient when you need to quickly attach a one-off IP to a profile without cluttering the global list. Importantly, the number of proxies used is unlimited—the tariff restrictions apply only to the number of saved proxies in the manager, but you can always apply as many temporary proxies as you want. This is flexible—you can store, for example, 100 frequently used proxies in the list and substitute other addresses "on the fly" for one-off tasks.
- Built-in Proxy Shop: One of Octo Browser's advantages is the availability of a proxy marketplace directly within the app. The so-called "Proxy Shop" allows you to buy proxies from trusted partners without leaving the browser. You save time searching for a reliable provider: simply open the proxy purchase tab, choose the desired provider and plan. At the time of writing, you can purchase residential proxies with traffic-based payment (per GB). Octo supports integration with any provider, offering a pool of tens of millions of IPs worldwide. For example, 2Captcha service, known for its CAPTCHA solutions, also offers proxies and claims to have over 90 million residential IPs in over 220 countries.
- Easy Proxy Integration into Profiles: After acquiring or adding proxies, attaching them to the desired profiles is very simple. Octo offers several ways to quickly link proxies to profiles: you can go to the "Proxies" section and click "New Proxy" or click on the proxy column in the profile list. Then, simply select one of the saved proxies from the list or paste a temporary one. If you're using Proxy Shop, there is an option to automatically generate proxy configurations for Octo: for example, 2Captcha provides ready-made links for popular anti-detect browsers, including OctoBrowser. In the 2Captcha cabinet, you select the "OctoBrowser" service and receive a pre-configured string that can be copied and directly pasted into Octo without additional setup. This "one-click" integration makes life easier, especially for beginners.
- Anonymity through the "Fingerprint + Proxy" Combination: Using high-quality residential proxies in combination with proper fingerprint spoofing yields maximum effectiveness. Residential proxies (IP addresses of regular home users) significantly increase trust from websites, as your traffic appears to be from a real person, not from a data center server. Octo Browser, configured for such IPs, helps minimize the risk of CAPTCHA appearance or mass IP bans. Combining Octo with good proxies allows bypassing CAPTCHA and IP blockages, even when running multiple accounts simultaneously. Of course, general precautions must also be observed: ensuring the uniqueness of profile behaviors, avoiding similar actions at the same time, etc. But from a technical perspective, Octo provides all the tools necessary for each profile to have its own IP, its own fingerprint, and appear as an independent user to external resources.
Conclusion
Octo Browser represents a comprehensive solution for those who need enhanced privacy and multi-accounting without hassle. Technically, it offers: a powerful system of isolated profiles with data encryption and team management, advanced fingerprint spoofing mechanisms (deeply integrated into the Chromium core and regularly updated), and flexible proxy handling (support for all protocols, a convenient manager, and an integrated marketplace of trusted proxy providers).
Importantly, Octo Browser does not limit itself to basic functionality: it offers an API for automation (allowing browser management through Puppeteer/Selenium scripts), support for all major platforms (Windows, macOS Intel/M1, Linux), fast Chrome engine updates, and quality support. All of this makes Octo one of the flagships among anti-detect browsers, a tool that meets the current security and anonymity requirements.
Thanks to the combination of a realistic digital fingerprint and a unique IP, each Octo Browser profile "blends in" with the crowd on the internet, allowing bypassing anti-fraud systems and freely engaging in arbitration, marketing, web scraping, or any other activity requiring multiple independent accounts. If your goal is to work online discreetly and effectively, Octo Browser provides all the necessary technical capabilities to achieve this goal.